
Have you ever noticed that while using your phone for say playing a video game or processing a video through a video
editing tool, it warms up? This means that certain data is being processed on your phone. However, the amount of voltage
applied to your phone by your battery is almost kept intact (let’s say 3.3 volts). This means that when processing
information, the amount of current supplied to your phone hardware changes. This amount of current varies in various
applications. So what does it means? It means that data processing is power dependent which is a security breach.
It has been shown by the researcher that the secret information on your electronic device can be stolen by just
looking at the power consumption profile of your electronic device. In principle, to breach security by exploiting
electronic devices to gather information from or influence the program execution of a system by measuring or
exploiting indirect effects of the system or its hardware -- rather than targeting the program or its code directly.
These attacks are known as side channel attacks (SCA).
The mentioned SCA-based attack example is a very well-studied attack in the literature. However, a few years ago
researchers found it is possible to steal secret information on electronic devices (more specifically chips) using a
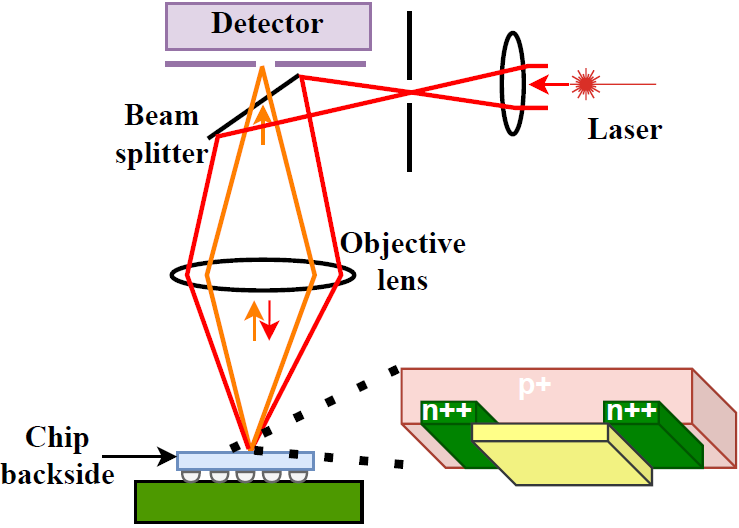
non-invasive laser beam. Since silicon materials are transparent to laser beams in the wavelength of the near-infrared
region (1100-1300nm), the laser light can travel to the terminals of each transistor. Then based on the voltage present
at each terminal of the transistor the reflected light gets modulated due to the strength of the electrical field at
each junction. As a result, when the light reflects, the indices of reflection and refraction of the incident light change.
Accordingly, based on the change in the indices of reflection and refraction, an attacker can deduce what voltage exists on
the transistor. This is a serious thread toward chips. The basic setup for an attack on the chip is shown below.
We are working on a
project called “OptiSecure” project.
An overview of our project is shown in the figure below.
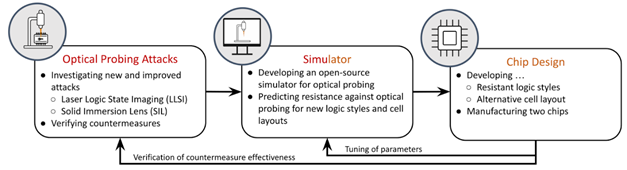
The general goal of our project is to investigate methods to prevent optical probing attacks. Our goal is to develop a
layout design using existing industry standard technology that is robust toward optical probing attack. As the first step,
we developed an optical probing simulator to find out which type of layout design leaks less information toward optical
probing. Then to prove the robustness of our layout toward optical probing, we taped-out a chip consisting of various designs.
Our chip includes more than 400 test structures that we would like to probe and see its robustness.
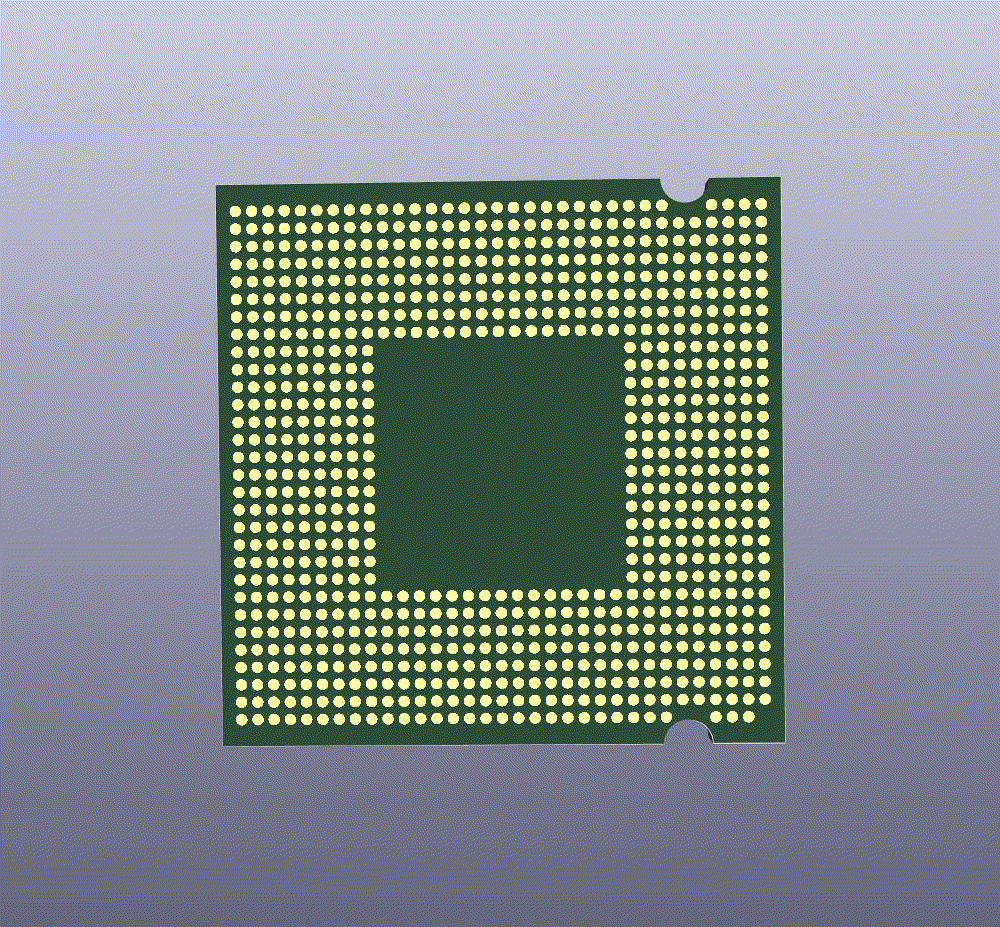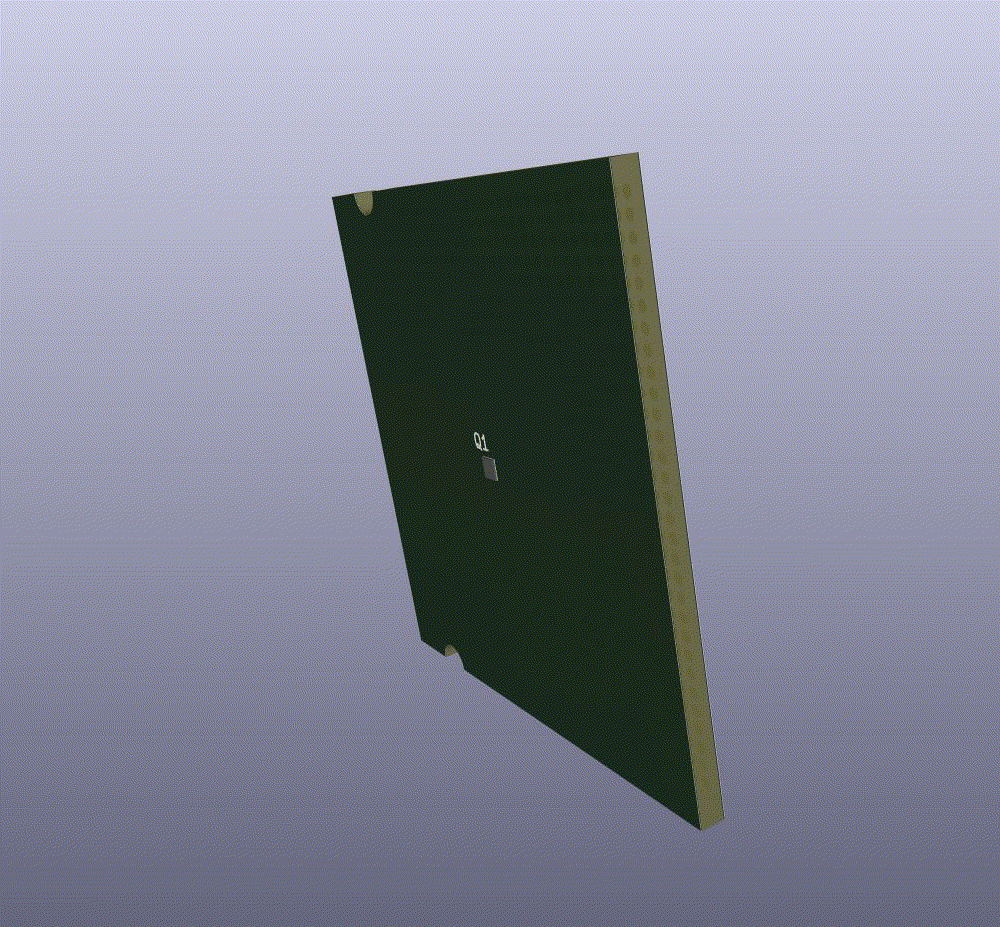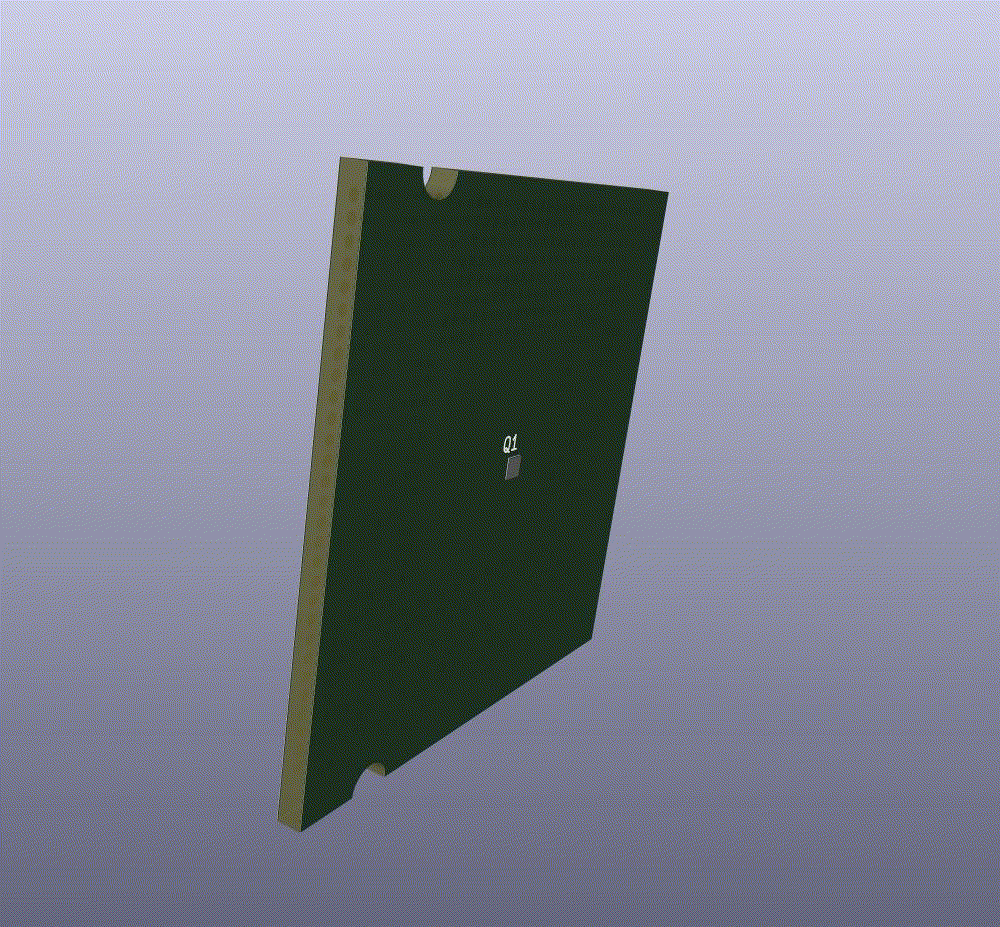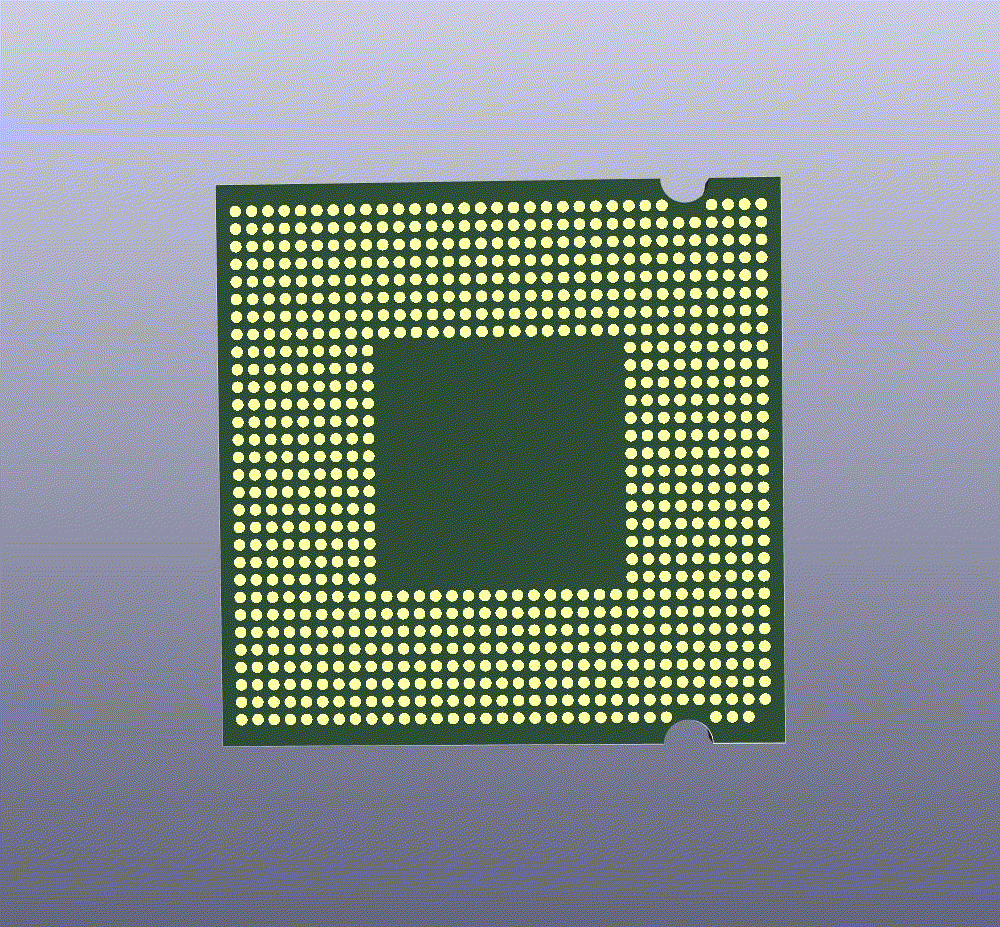
Next, we would like to perform an attack on our chip. Then based on our findings from attacking our chip, we will import
the reflection values from our chip to our simulator. This will enable our simulator to work more accurately. This feedback
loop in our project namely, “OptiSecure” will result in generating accurate optical probing simulation. As a result, by
incorporating the results from our optically probed chip, and simulator, we can propose layout styles that are more robust
against optical probing attacks.
Besides using optical probing to attack a chip to steal the intellectual property of a chip, we proposed the use of optical
probing to defend a chip against trojan insertion. The scenario is when a design house outsources its design to a foundry
abroad for fabrication, there is a possibility that the foundry is untrusted and inserts a hardware trojan in your design.
Publications | Conferences:
Sajjad Parvin, Mehran Goli, Frank Sill Torres, Rolf Drechsler,
“FELOPi: A Framework for Simulation and Evaluation of
Post-Layout File Against Optical Probing”, Design, Automation and Test in Europe (DATE) ,Antwerp, Belgium, 2023
Sajjad Parvin, Mehran Goli, Frank Sill Torres, Rolf Drechsler,
“Trojan-D2: Post-Layout Design and Detection of
Stealthy Hardware Trojans - a RISC-V Case Study “,28th Asia and South Pacific Design Automation Conference (ASP-DAC),
Tokyo, Japan, 2023
Sajjad Parvin, Thilo Krachenfels, Shahin Tajik, Jean-Pierre Seifert, Frank Sill Torres and Rolf Drechsler ,
”Toward
Optical Probing Resistant Circuits: A Comparison of Logic Styles and Circuit Design Techniques”, Asia and South Pacific
Design Automation Conference (ASP-DAC) Referenz: Taipei, Taiwan, 2022
 Have you ever noticed that while using your phone for say playing a video game or processing a video through a video
editing tool, it warms up? This means that certain data is being processed on your phone. However, the amount of voltage
applied to your phone by your battery is almost kept intact (let’s say 3.3 volts). This means that when processing
information, the amount of current supplied to your phone hardware changes. This amount of current varies in various
applications. So what does it means? It means that data processing is power dependent which is a security breach.
It has been shown by the researcher that the secret information on your electronic device can be stolen by just
looking at the power consumption profile of your electronic device. In principle, to breach security by exploiting
electronic devices to gather information from or influence the program execution of a system by measuring or
exploiting indirect effects of the system or its hardware -- rather than targeting the program or its code directly.
These attacks are known as side channel attacks (SCA).
Have you ever noticed that while using your phone for say playing a video game or processing a video through a video
editing tool, it warms up? This means that certain data is being processed on your phone. However, the amount of voltage
applied to your phone by your battery is almost kept intact (let’s say 3.3 volts). This means that when processing
information, the amount of current supplied to your phone hardware changes. This amount of current varies in various
applications. So what does it means? It means that data processing is power dependent which is a security breach.
It has been shown by the researcher that the secret information on your electronic device can be stolen by just
looking at the power consumption profile of your electronic device. In principle, to breach security by exploiting
electronic devices to gather information from or influence the program execution of a system by measuring or
exploiting indirect effects of the system or its hardware -- rather than targeting the program or its code directly.
These attacks are known as side channel attacks (SCA).
 Next, we would like to perform an attack on our chip. Then based on our findings from attacking our chip, we will import
the reflection values from our chip to our simulator. This will enable our simulator to work more accurately. This feedback
loop in our project namely, “OptiSecure” will result in generating accurate optical probing simulation. As a result, by
incorporating the results from our optically probed chip, and simulator, we can propose layout styles that are more robust
against optical probing attacks.
Next, we would like to perform an attack on our chip. Then based on our findings from attacking our chip, we will import
the reflection values from our chip to our simulator. This will enable our simulator to work more accurately. This feedback
loop in our project namely, “OptiSecure” will result in generating accurate optical probing simulation. As a result, by
incorporating the results from our optically probed chip, and simulator, we can propose layout styles that are more robust
against optical probing attacks.